SoC design for security has grown and evolved over time to address numerous potential threat sources. Many countermeasures have arisen to deal with ways hackers can gain control of systems through software or hardware design flaws. The results are things like improved random number generators, secure key storage, crypto, and memory protection. Also, SoCs have added hardware security modules, secure boot chain, dedicated privileged processors, etc. However, one method of attack is often overlooked – side channel attacks. Perhaps this is because the relative risk and difficulty of such attacks has been underestimated.
In an upcoming webinar Tim Ramsdale, CEO of Agile Analog, offers a sober look at the threat from side-channel attacks on SoCs. The Webinar titled “Why should I care about Side-Channel Attacks on my SoC?” not only explains that they are a greater threat than often believed, but it also offers an effective solution to the problem.
You only need to look at YouTube to find presentations made at Defcon events that illustrate how RISC-V based SoCs, Apple Airtags or ARM Trustzone-M devices are vulnerable to glitching attacks. Your first thought is that this might be done with some lucky timing achieved with touching bare wires, pushing a button randomly or requires a completely instrumented forensics lab. If that were the case, the threat would be so minimal that it might be possible to ignore. Tim points out that there is an open source kit available from Mouser to automate and make these attacks systematic. This kit comes with a microprocessor & easy to use UI, and is capable of clock and power attacks.
The webinar explains how these attacks can be carried out and why they represent a bigger threat than you might think. Imagine, if in your device an attacker can randomly flip the state of any one single register – such as a security bit? Suppose the result of a BootROM checksum can be corrupted? Varying voltage and clock signals for extremely short periods of time can cause otherwise undetectable changes in state leading to access that could allow running malicious code in privileged mode.
Additionally, access gained through these techniques can allow hackers to explore other weaknesses in your system. With the knowledge gained through a one-off side channel attack, a more easily repeated exploit could be discovered – one that does not require direct contact with the targeted device. IoT devices are also particularly vulnerable, as they are connected and often exposed to physical contact.
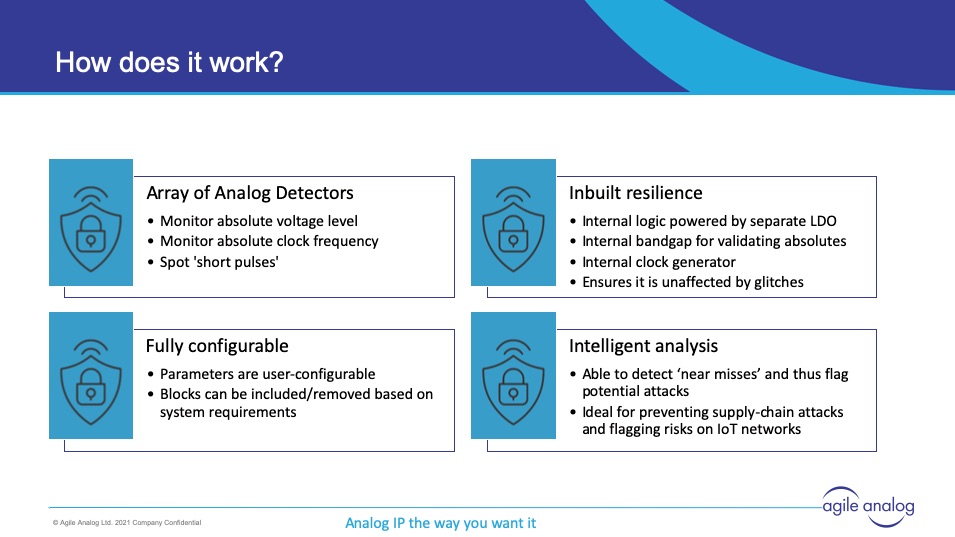
Agile Analog has developed a solution to detect side-channel attacks. They have sets of sensors that are capable of detecting the kinds of effects that occur when clocks or power pins are tampered with. Their side channel attack protection blocks have their own internal LDO and clock generators to ensure they can operate during attacks. The control, analysis and monitoring logic is easy to integrate with SoC security modules.
During the webinar Tim explains the details of how their solution can monitor and report attacks or even attempted attacks. This can include attacks that occur in the supply chain before the device is added to the finished system. This webinar is informative and provides useful information on enhancing SoC security. Here is the REPLAY.
Also read:
CEO Interview: Barry Paterson of Agile Analog
Counter-Measures for Voltage Side-Channel Attacks
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.