
It is well-known that there is more data being generated all the time. The need to store and process that data with less power and higher throughput dominates design considerations for virtually all systems. There is another dimension to the problem – ensuring the data is secure as all this movement and processing occurs. Within computing systems, the Peripheral Component Interconnect Express, or PCIe standard is the de-facto method to move data. This standard has gained tremendous momentum. If you’d like to peruse the various versions of the standard, I recommend you visit the PCI SIG website. The considerations for how to secure PCIe channels and how to verify the robustness of those channels is the subject of this post. The options to consider are many, as are the technical requirements to design and validate a robust architecture. The good news is that a market leader has published a white paper to help guide you. Let’s see how Siemens EDA offers a comprehensive guide to PCIe transport security.
Framing the Problem
The concept of a secure PCIe link is easy to imagine. Making it work reliably with real world constraints is not as easy, however. It turns out there are many tradeoffs to face, and many decisions to make. And once you’ve done that, verifying the whole thing will work reliably is yet another challenge. As I read the white paper from Siemens EDA, I got an appreciation for the complexity of this task. If you plan to use PCIe channels in your next design, you’ll want to get a copy. A link is coming, but first let’s look at some of the items covered.

The white paper is written by Suprio Biswas, an IP Verification Engineer at Siemens EDA. He has been working in the field of digital design and communication at Siemens EDA for over four years and has presented his work at a recent PCI-SIG conference. Suprio has a knack for explaining complex processes in an approachable way. I believe his efforts on this new white paper will help many design teams.
Before we get into some details, I need to define two key terms that will pop up repeatedly in our discussion:
- Security protocol and data model (SPDM) specification – defines a message-based protocol to offer various security processes for authentication and setting up a secure session for the flow of encrypted packets.
- Component measurement and authentication (CMA) – defines a mapping of the SPDM specification for PCIe implementation.
With that out of the way, let’s look at some topics covered in the white paper.
Some Details
The white paper begins with an overview of the topics to consider and the decisions that need to be made. Authentication, access control, data confidentiality/integrity and nonrepudiation are discussed. This last item prevents either the sender or the receiver from denying the transmission of a message. There is a lot of coordination to consider among these topics.
The aspects of implementation are then covered. This discussion centers on the various approaches to encryption, decryption and how keys are handled. The design considerations to be made are inter-related. For example, there can be a single key (secret key), or a pair of keys (public key and private key) based on the chosen cryptographic algorithm.
Getting back to the terms defined above, there is a very useful discussion about implementing security through the CMA/SPDM flow. There are many considerations to weigh here and trade-offs to be made. It is best to read the white paper and get the direct guidance of Suprio. To whet your appetite, below is a high-level CMA/SPDM flow for establishing a secure connection.
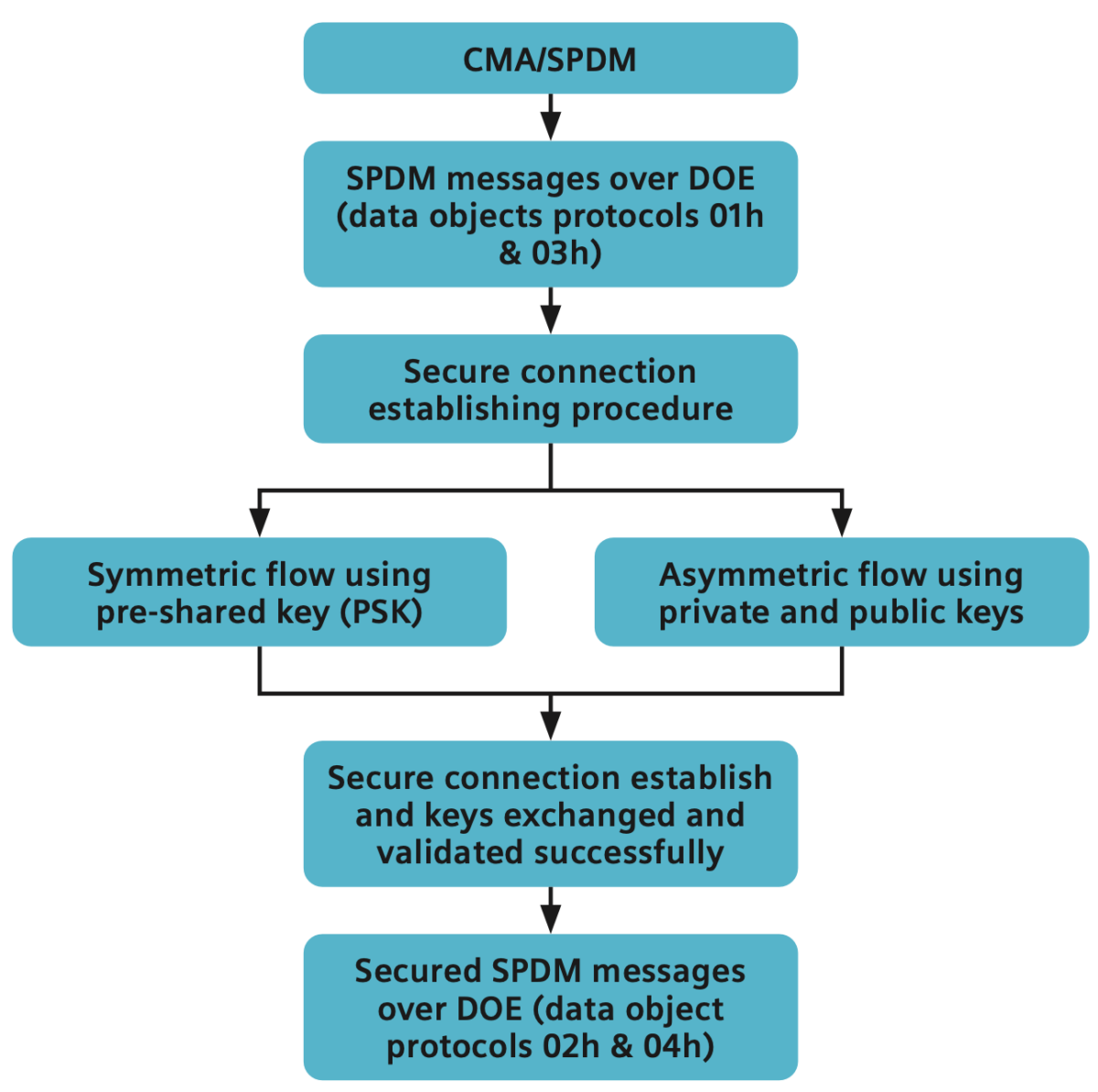
Suprio then covers the Siemens Verification IP (VIP) for PCIe. This IP verifies designs that test the successful establishment of a secure connection through CMA/SPDM before starting the flow of encrypted packets. The IP is compliant with the CMA Revision 1.1 specification and SPDM version 1.3.0 specification.
Many more details are provided in the white paper.
To Learn More
If you’d like to learn more about PCIe Gen6 verification, you can find that here. And finally, download your own copy of this valuable white paper here. You will find it to be a valuable asset for your next design. And that’s how Siemens EDA offers a comprehensive guide to PCIe transport security.
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.