 This topic is inspired by a presentation at last year’s DAC presented by Methodics, now part of Perforce. The issues raised by the original presentation are still quite relevant in the current business climate. IP leakage is something everyone should consider as part of their normal business operations. Your design IP really IS the essence of your business and you should protect it. Let’s assume for the sake of argument that your IP portfolio is probably leaking. What can you do about it?
This topic is inspired by a presentation at last year’s DAC presented by Methodics, now part of Perforce. The issues raised by the original presentation are still quite relevant in the current business climate. IP leakage is something everyone should consider as part of their normal business operations. Your design IP really IS the essence of your business and you should protect it. Let’s assume for the sake of argument that your IP portfolio is probably leaking. What can you do about it?
We live in a highly connected and distributed world which fosters lots of cracks and holes that can create leaks. Now that Methodics is part of Perforce, the focus on this problem has become broader and more comprehensive. Check out a podcast Dan and I recently did that explains the story behind combining Methodics and Perforce if you’d like some more context.
Let’s begin with IP export rules. Export Administration Regulations (EAR) cover commercial and government items and International Traffic in Arms Regulations (ITAR) cover export of defense items. These rules govern IP export and are much broader than most people realize. To set the stage, IP is considered exported if:
- It is shipped internationally into a restricted geography
- It is ‘conveyed’ to a foreign national of a restricted geography even within the US
- It is released from one foreign (potentially unrestricted) geography into a restricted geography
You should start seeing lots of shades of gray at this point. Let’s look at some definitions of IP leakage:
- IP can leak if it is “exported” as defined by EAR without a valid export license
- IP can leak if it is covered by ITAR and is “disclosed” to an unauthorized person
- Beyond EAR and ITAR, IP can leak if it is considered confidential or “trade secret” within the organization, and is exposed beyond employees who need to know
The DAC presentation from Methodics had an informative graphic that portrayed what could happen during a routine trip (assuming we ever travel again). The scenario described is quite familiar:
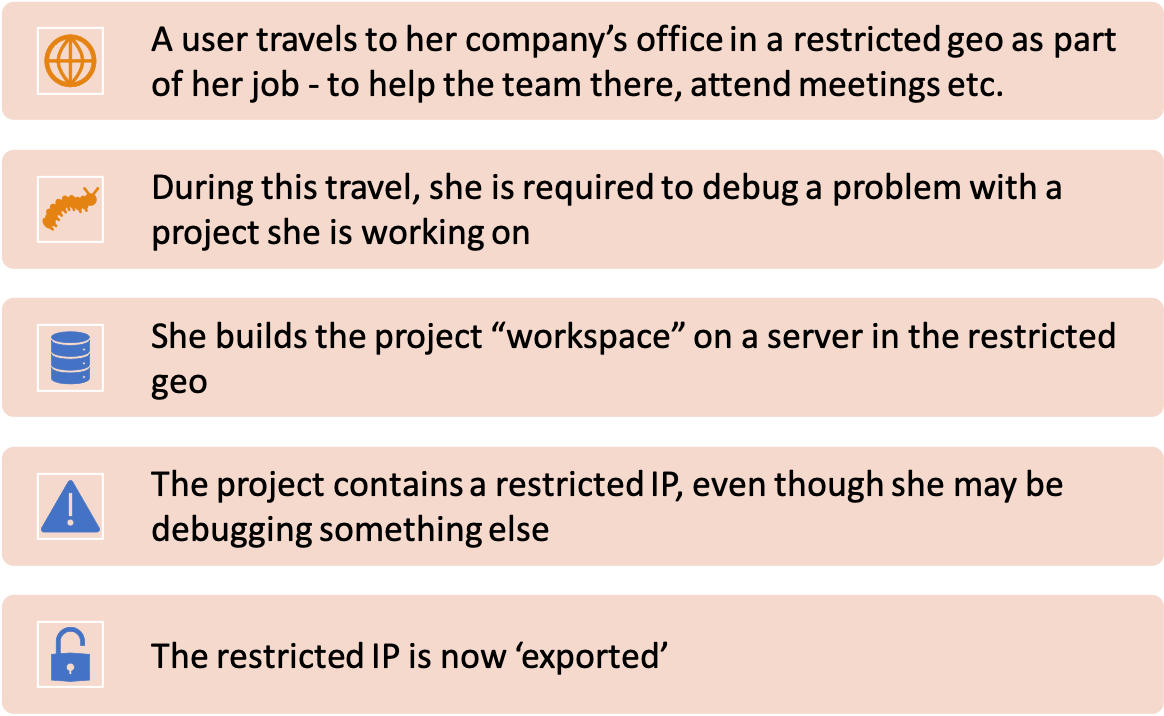
“Accidental export” can result in heavy fines and significant business disruption. According to the Bureau of Industry and Security, export control fines since 2000 total $2.2B. Based on publicly available information, semiconductor companies such as Intel, Dell/EMC, Lattice, Infineon and Maxim have been impacted. This can happen to you and your company.
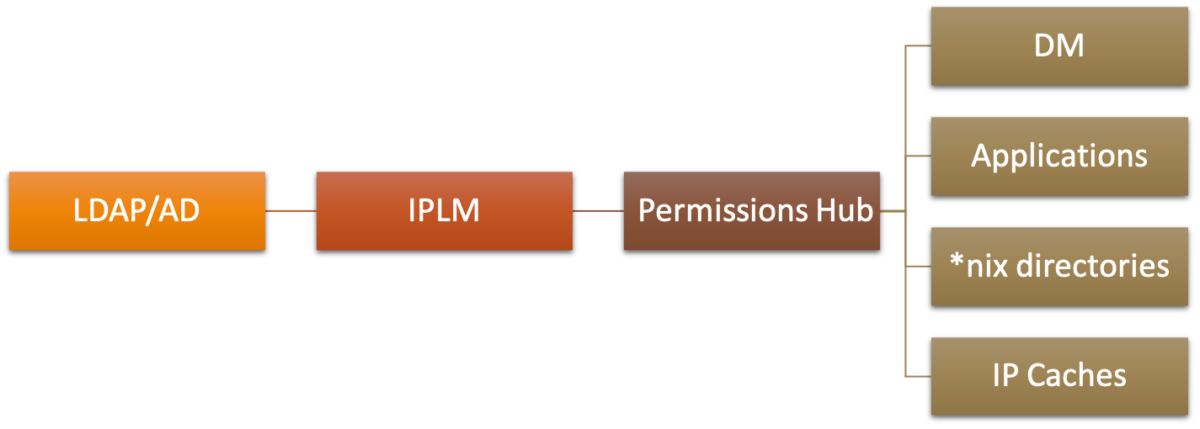
What can be done to avoid all this? As you might imagine Perforce and Methodics have some excellent ideas. To start with, IP access control needs to be consolidated. No more multiple, disjoint systems across the enterprise. There is simply no way of ensuring a consistent approach with this situation. Some of the key points offered in the Methodics DAC presentation includes:
- Consolidate Access Control with IP-centric processes
- IP R/W permissions drive access control to all systems
- Managing lightweight directory access protocol (LDAP) / active directory (AD) group membership automatically propagates across the enterprise
Graphically, it looks like this:
The concept of geofencing is useful here as well. Geofencing restricts IP availability in certain geographies regardless of access. An IP Lifecycle Management (IPLM) system can enable geofencing with the following capabilities:
- Allow IPs to carry ‘include’ and ‘exclude’ lists of geographies
- Restrict IPs, regardless of access, based on these lists
- IP data cannot reside in user workspaces or caches in these restricted geographies
- IP meta-data cannot be visible or extracted in these geographies
IPLM systems should also preserve IP hierarchies, preventing IPs from being flattened into a single object or code base. If this occurs, insidious embedded IPs can be exported without the user’s knowledge. This approach also allows IPs and their versions to be tracked even when used as part of another hierarchy. Note that the rest of the hierarchy may be “safe”, but key IPs need to be restricted. A centralized approach is the way to accomplish this.
Stopping IP leakage requires a comprehensive system, and it cannot be solved by any single action. The overall goal is to know who used which version of which IP in what context at all times. You can learn more about how Methodics can help you manage your IP throughout your development lifecycle in their upcoming webinar, IP Security: Protecting Your Most Important IP Assets With Methodics IPLM. Your IP portfolio is probably leaking, and now you know what you can do about it.
Also Read:
Perforce Embedded DevOps Summit 2021 and the Path to Secure Collaboration on the Cloud
Single HW/SW Bill of Material (BoM) Benefits System Development
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.