As I read both the popular and technical press each week I often see articles about computer systems being hacked, and here’s just a few vulnerabilities from this week:
- Global phone hacks expose darker side of Israel’s startup nation image
- How Taiwan is trying to defend against a cyber World War III
- Kaseya receives decryption key after ransomware attack
Here on SemiWiki we have many engineers responsible for SoC hardware, software, firmware and security, so what are the best practices to make your new or existing electronic systems more hardened against attacks, and less vulnerable?
Gajinder Panesar and Tim Ramsdale are two experts from Siemens EDA and Agile Analog, respectively, and they teamed up to write a 15 page White Paper, “The Evolving Landscape of SoC vulnerabilities and analog threats.” I’ll share the gist of what I learned from reading this.
Vulnerabilities
One security premise is that relying only on software updates to patch vulnerabilities is not sufficient, so adding security as part of the hardware design should be considered. There’s even an Open source project called OpenTitan, to help you build a transparent, high-quality reference design and integration guidelines for silicon root of trust (RoT) chips. With a hardware-based RoT, only firmware compared against a known signature can be run, stopping attempts to load any hacked firmware.
Hackers are becoming creative and resourceful enough to examine the secret keys in an RSA algorithm by making hardware measurements, noting small variations in how operations are executed, aka side-channel attack. Shown below are four multiplication portions by the purple arrows, then the negative spikes are part of the squaring and modular reduction in the algorithm.
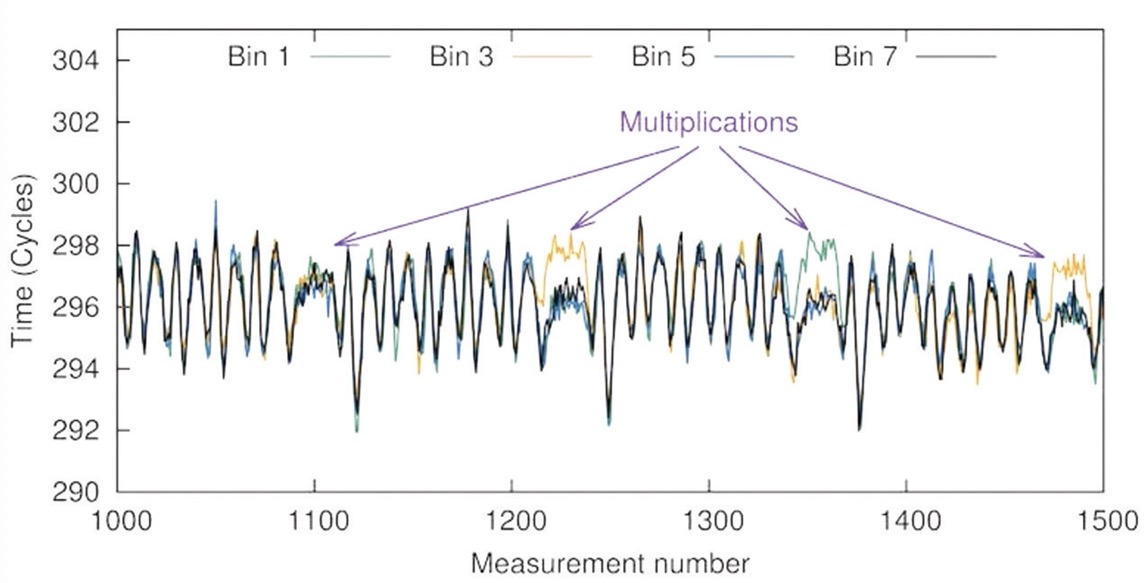
Security clues can be revealed by examining several things:
- Cache activity
- Execution pipelines
- Electromagnetic (EM) values
- Voltage variations
- Current variations
Another example of a side-channel attack has the hacker trying to guess one of the key bytes, and around region 350 they found one correct key byte.
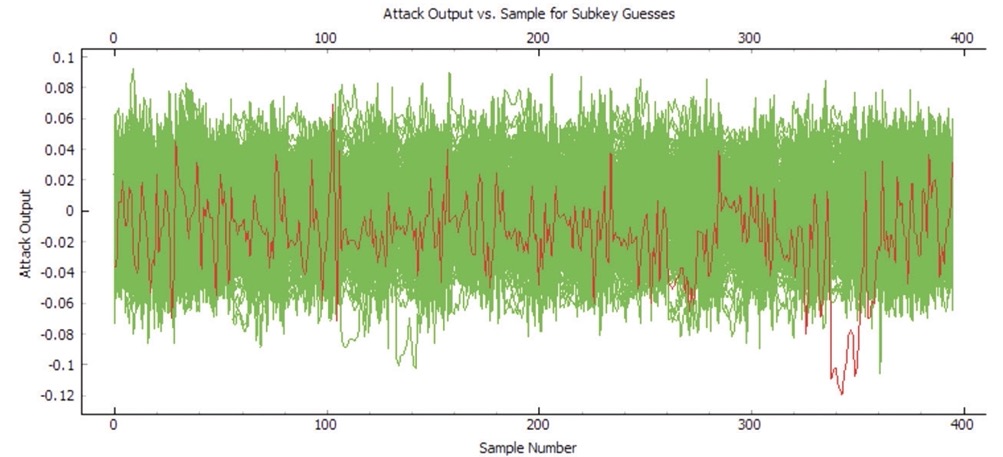
Targets for hacking include 5G infrastructure, edge servers, IoT devices, cloud computing, autonomous vehicles, industrial robotics. Hackers are using statistical approaches to measure electronic devices, providing clues to security vulnerabilities. One counter-measure is for the hardware design team to add random electrical noise.
Another technique that hackers use is to intentionally glitch the power supply at a specific time point, which can then flip a stored bit into an unsafe state, as documented by German security company LevelDown. Even some older processors had an exploit where a hacker used illegal opcodes, which in turn put the processor into a vulnerable state.
Temperature is yet another technique where an attacker can run a SoC at a higher or lower temperature than specified, in order to alter the internal state or even extract private keys from a physically unclonable function (PUF).
An attacker may use voltage changes to the supply rail, in order to slow down or speed up the logic, causing internal bits to flip, and illegal states to be reached.
If a hacker has physical access to your electronic system, them directly controlling the clock inputs by changing the duty cycle, or introducing glitches will change the internal logic. ChipWhisperer is a company with an open-source system to expose weaknesses from embedded systems, using side-channel power analysis and fault injection.
Fault injection using electromagnetic (EM) radiation is a technique used by ChipShouter, but they would have to be precisely timed with internal clock edges to create a repeatable fault. Even using a laser light on a de-capped IC package can force internal errors for an SoC.
Countermeasures to Vulnerabilities
- Clock glitches: Internally generated source for comparison.
- Power glitches: Brownout detectors
- Temperature attack: Temperature sensors
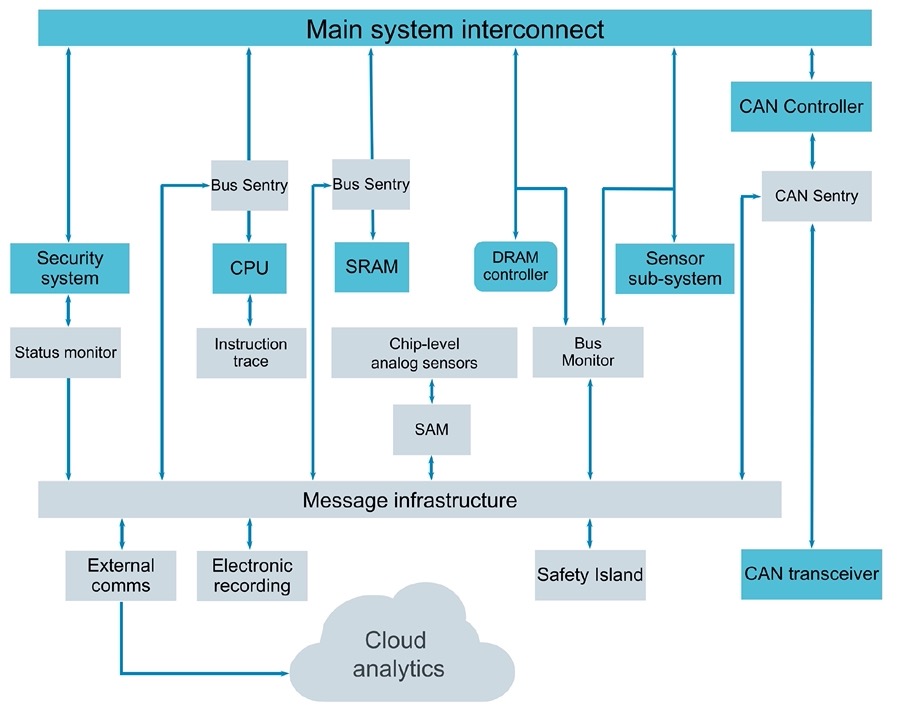
At Siemens EDA they offer a product called Tessent Embedded Analytics, and it embeds hardware monitors in your SoC, then communicates with a message-based architecture. Adding hardware security IP from Agile Analog provides checks on clock, voltage and temperature:
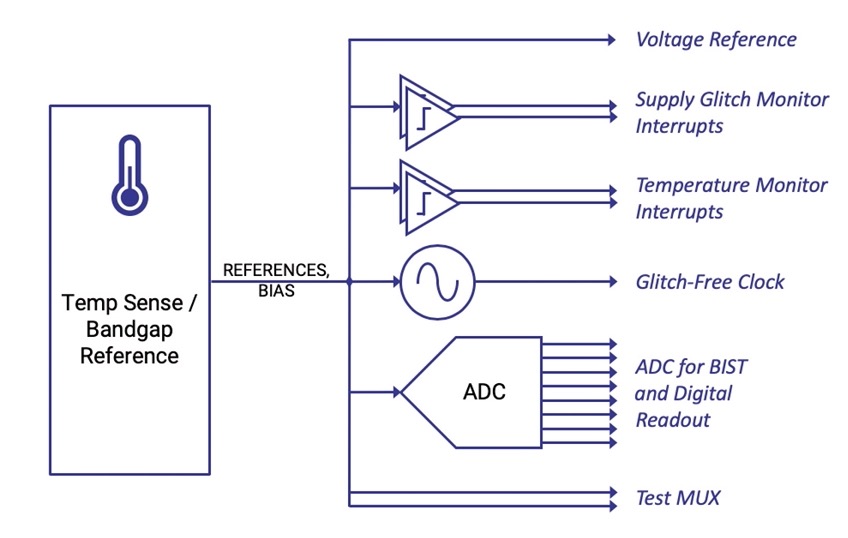
These monitors can sense an exploit, then the embedded analytics can both report and decide the appropriate security response. The combination of embedded analytics and security IP shown in a diagram:
Summary
The great power and benefits of SoC design are under attack from hackers, so it is up to the design community to adopt pro-active measures to harden the security level of their new products. What Siemens EDA and Agile Analog have created is a framework of embedded digital and analog hardware, to enable detection of cyber threats, and a means to take appropriate action, in real time.
Yes, this means more work for your design team, but your customers will place a higher value on a more secure SoC. You don’t have to start from scratch either, because Siemens EDA and Agile Analog have done the ground work for you.
To read the full 15 page White Paper, visit this page and provide a few details about yourself.






Comments
There are no comments yet.
You must register or log in to view/post comments.