Security is a slippery topic. We all agree that “something should be done”, but most of us are waiting for someone else to lead the way. There’s no shortage of proprietary solutions, though given the distributed nature of the problem it’s difficult to see how those separately or collectively can rise to the occasion. What we really… Read More
IoT’s Inconvenient Truth: IoT Security Is a Never-Ending Battle
The continued innovation and widespread adoption of connected devices — the internet of things (IoT) — has resulted in a vast range of conveniences that improve our lives every day. At the same time, the ubiquity of IoT devices, which market watchers estimate to be in the tens of billions, also makes it more attractive to bad actors… Read More
Fuzzing to Validate SoC Security. Innovation in Verification
Fuzzing is to software verification what randomization is hardware verification. Can a fuzzing approach improve hardware security testing? Paul Cunningham (GM, Verification at Cadence), Raúl Camposano (Silicon Catalyst, entrepreneur, former Synopsys CTO) and I continue our series on research ideas. As always, feedback… Read More
What is a Data Lake?
“Data Lake” is a massive, easily accessible data repository for storing “big data”. Unlike traditional data warehouses, which are optimized for data analysis by storing only some attributes and dropping data below the level aggregation, a data lake is designed to retain all attributes, especially when you do… Read More
Your Car Is a Smartphone on Wheels—and It Needs Smartphone Security
Your modern car is a computer on wheels—potentially hundreds of computers on a set of wheels. Heck, even the wheels are infested with computers—what do you think prompts that little light on your dashboard to come on if your tire pressure is low? And computers don’t just run your infotainment system, backup camera, dashboard warning
Webinar: How to Protect Sensitive Data with Silicon Fingerprints
Data protection is on everyone’s mind these days. The news cycle seems to contain a story about hacking, intrusion or cyber-terrorism on a regular basis. The cloud, our hyperconnected devices and the growing reliance on AI-assisted hardware to manage more and more mission critical functions all around us make data protection… Read More
CEO Interview: Pim Tuyls of Intrinsic ID
Pim Tuyls, CEO of Intrinsic ID, founded the company in 2008 as a spinout from Philips Research. It was at Philips, where he was Principal Scientist and managed the cryptography cluster, that he initiated the original work on Physical Unclonable Functions (PUFs) that forms the basis of the Intrinsic ID core technology. With more… Read More
Falsely Vilifying Cryptocurrency in the Name of Cybersecurity
I get frustrated by shortsighted perceptions, which are misleading and dangerous is far easier to vilify something people don’t fully understand.
Here is another article, titled Bitcoin is Aiding the Ransomware Industry, published by Coindesk, implying cryptocurrency is the cause of digital crime.
This is one of many such… Read More
CEO Interview: Lee-Lean Shu of GSI Technology
Lee-Lean Shu co-founded GSI Technology in March 1995 and has served as President and Chief Executive Officer and as a member of the Board of Directors since its inception. In October 2000, Mr. Shu became Chairman of the Board of GSI Technology. Mr. Shu was has held various management positions in SRAM and DRAM designs at Sony Microelectronics… Read More
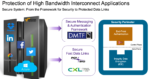
The Heart of Trust in the Cloud. Hardware Security IP
You might think that cloud services run on never-ending racks of servers and switches in giant datacenters. But what they really run on is trust. Trust that your data (or your client’s data) is absolutely tamper-proof inside that datacenter. Significantly more secure than it would be if you tried to manage the same operations in… Read More










Advancing Automotive Memory: Development of an 8nm 128Mb Embedded STT-MRAM with Sub-ppm Reliability