The rapid escalation of cyberattacks over the past two decades has exposed a fundamental weakness at the core of modern computing systems: the lack of memory safety. Industry data consistently shows that the majority of critical software vulnerabilities stem from memory corruption issues such as buffer overflows, use-after-free… Read More
Securing RISC-V Third-Party IP: Enabling Comprehensive CWE-Based Assurance Across the Design Supply Chain
by Jagadish Nayak
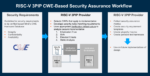
RISC-V adoption continues to accelerate across commercial and government microelectronics programs. Whether open-source or commercially licensed, most RISC-V processor cores are integrated as third-party IP (3PIP), potentially introducing supply chain security challenges that demand structured,… Read More
Caspia Technologies Unveils A Breakthrough in RTL Security Verification Paving the Way for Agentic Silicon Security
In a significant advancement for the semiconductor industry, Caspia Technologies announced the broad availability of CODAx V2026.1, its flagship RTL security analyzer. The new release strengthens early-stage hardware security verification and positions the company to deliver fully agentic workflows that automate vulnerability… Read More
PQShield on Preparing for Q-Day
Following my series on quantum computing (QC), it is timely to look again at what is still the most prominent real-world concern around this technology: its ability to hack classical security methods for encryption and related tasks. Given what I have written on the topic, an understandable counter would be that QC is still in development… Read More
2026 Outlook with Richard Hegberg of Caspia Technologies
Tell us a little bit about yourself and your company
I’m Rick Hegberg and I’ve been CEO of Caspia Technologies since 2024. I have a deep semiconductor background, including CEO roles at three semiconductor start-ups and executive roles at SanDisk/WD, Qualcomm, Atheros, Numonyx/Micron, ATI/AMD, and VLSI Technology.
Throughout… Read More
Webinar: Why AI-Assisted Security Verification For Chip Design is So Important
It is well-known that AI is everywhere, and the incredible power of this new technology is enabled by highly complex, purpose-built silicon. But there is a silent enemy of this substantial, world-changing progress. Something that has the power to steal a bright future from all of us. The hardware root of trust for those advanced… Read More
The Quantum Threat: Why Industrial Control Systems Must Be Ready and How PQShield Is Leading the Defense
Industrial control systems (ICS) underpin the world’s most critical infrastructure: power grids, manufacturing plants, transportation networks, water systems, oil and gas facilities, and chemical processing operations. For decades, these systems relied on isolation, proprietary communication protocols, and hardware… Read More
A Six-Minute Journey to Secure Chip Design with Caspia
Hardware-level chip security has become an important topic across the semiconductor ecosystem. Thanks to sophisticated AI-fueled attacks, the hardware root of trust and its firmware are now vulnerable. And unlike software security, an instantiated weakness cannot be patched. The implications of such vulnerabilities are… Read More
Think Quantum Computing is Hype? Mastercard Begs to Disagree
Just got an opportunity to write a blog on PQShield, and I’m delighted for several reasons. Happy to work with a company based in Oxford and happy to work on a quantum computing-related topic, which you’ll find I will be getting into more deeply over coming months. (Need a little relief from a constant stream of AI topics.) Also important,… Read More
Podcast EP316: An Introduction to Hardware Security Modules (HSMs) and Marvell’s Unique LiquidSecurity Offering with Bill Hagerstrand
Daniel is joined by Bill Hagerstrand, director of Security Business at Marvell Technology where he manages the market-leading Marvell LiquidSecurity® HSM business. Bill has more than 20 years of experience in the semiconductor, AI/machine learning, and security markets.
Bill explains what an HSM is, how it is configured and… Read More










CEO Interview with Jerome Paye of TAU Systems