Cryptography serves the purpose for privacy, authentication, integrity, non-repudiation, and key exchange. With Cryptography plaintext is encrypted into ciphertext which will be decrypted back to usable plaintext.
Cryptography algorithms can be classifieds into 3 types:
- Secret Key Cryptography (SKC): It uses a single key for both encryption and decryption; also called symmetric encryption. It is used primarily for privacy and confidentiality.
- Public Key Cryptography (PKC): It uses one key for encryption and another for decryption; also called asymmetric encryption. It is used for authentication, non-repudiation and key exchange.
- Hash Functions: It uses a mathematical transformation to encrypt information, providing a digital fingerprint. It is used for message integrity.
The block ciphers are schemes for encryption or decryption where a block of plaintext is treated as a single block and is used to obtain a block of ciphertext with the same size. Advanced Encryption Standard (AES) is popular and widely used symmetric encryption algorithm for block encryption. It was developed by NIST to replace Data Encryption Standard (DES) as its key size was small. With increasing computing power, DES was considered vulnerable against exhaustive key search attack. AES is a block cipher that encrypts and decrypts 128 bits of data and is faster than DES. It is a subset of Rjindael block cipher and is used in wireless communication, IOT, encrypted data storage.
The size of an AES block is 128 bits, whereas the size of the encryption key can be 128, 192 or 256 bits. AES is based on substitution–permutation network. It comprises of a series of linked operations, some of which involve replacing inputs by specific outputs (substitutions) and others involve shuffling bits around (permutations). AES performs all its computations on bytes rather than bits. Hence, AES treats the 128 bits of a plaintext block as 16 bytes. Number of rounds in AES is variable and depends on size of the key. AES has 10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys. Each of these rounds uses a different 128-bit round key, which is calculated from the original AES key.
Block Ciphers can work in different modes of operation. A mode of operation tells how to repeatedly apply a cipher’s block operation to data larger than a block. AES can work in following modes of operation:
- Electronic Code Book (ECB) mode
It is the simplest mode. Each block of plain text is encrypted separately which enables parallel encryption of multiple blocks using multiple threads.
- Cipher Block Chaining (CBC) mode
In CBC encryption mode each plaintext block is XORed with ciphertext that was previously produced. Every subsequent ciphertext depends on the previous one. The first plaintext block is XORed to a random initialization vector. Encryption can be performed by only one thread.
- Cipher FeedBack (CFB) mode
It is similar to CBC mode. The difference is that ciphertext output of previous block is encrypted and then XORed with plaintext.
- Output FeedBack (OFB) mode
The OFB mode makes a block cipher into a synchronous stream cipher. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext.
- Counter (CTR) mode
CTR mode turns block cipher into a stream cipher. In counter mode of operation, the value of a counter is used as an initialization vector. Both encryption and decryption can be performed using multiple threads at the same time.
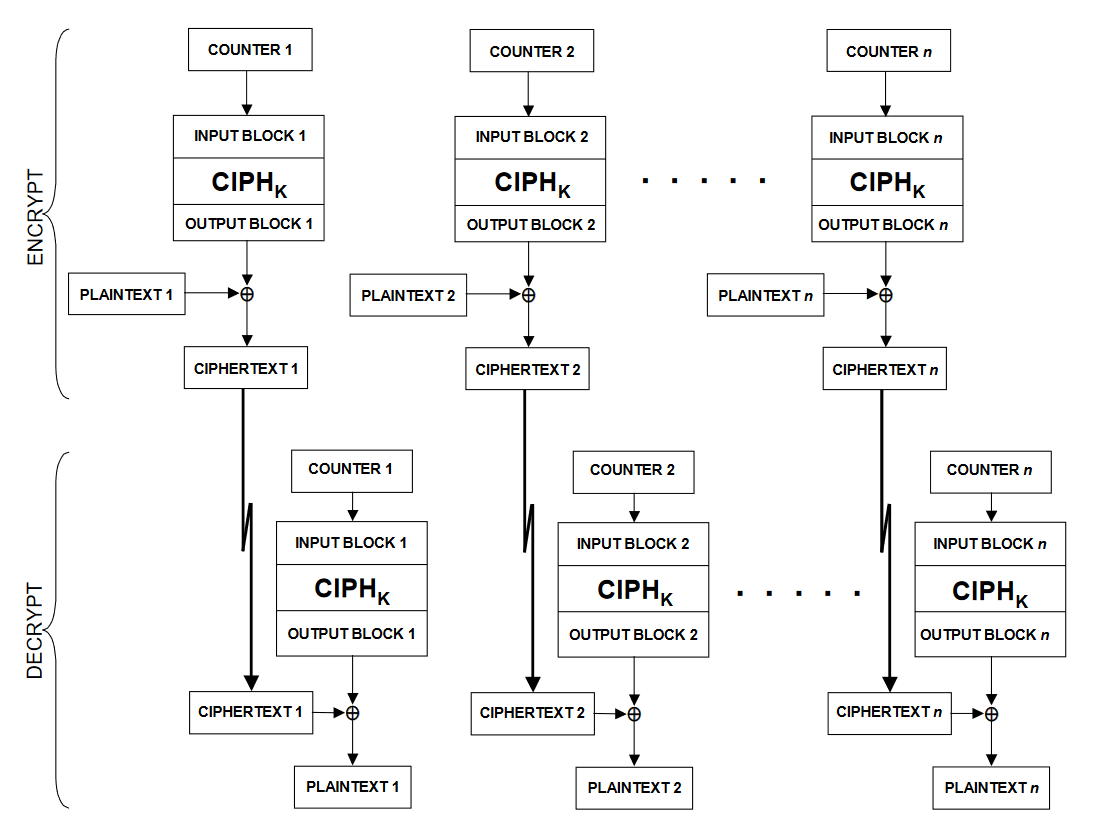
Figure 1 CTR mode of operation
AES IP cores are available from various IP vendors. These IP cores speed the design cycle and increase design quality. They are available with following features:
- Synchronous Design
- Pipelined Architecture
- Functional and Synthesizable
- High speed and throughput
- Scalable architecture
Synopsys DesignWare AES-GCM/CTR Core implements the AES-GCM/CTR algorithm as specified in the National Institute of Standards and Technology (NIST) Special Publication 800-38D, “Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC.” The implementation of a secure communications design requires the ability to do both cipher operations and message authentication. Authenticated encryption ensures that the ciphertext hasn’t been tampered with by an attacker. GCM is an authenticate and encrypt block cipher mode. It uses the Advanced Encryption Standard (AES) algorithm in counter mode (CTR) and a high-performance MAC algorithm based on Galois Field multiplication with CTR mode encryption, which can be pipelined for high throughput operations. It is a pipelined core and is capable of encrypting and decrypting at high speed. For message authentication, the GCM makes use of binary Galois Field multiplications that can be computed in parallel with the encrypt/decrypt operations. The core is available with key sizes of 128, 192 and 256 bits.
References:
https://csrc.nist.gov/publications/detail/sp/800-38a/final
https://www.synopsys.com/designware-ip/security-ip/cryptography-ip.html
https://www.synopsys.com/dw/ipdir.php?ds=security-aes-gcm-ctr
Share this post via:













Facing the Quantum Nature of EUV Lithography