In today’s digital landscape, data security has become an indispensable feature for any data transfer protocol, including Peripheral Component Interconnect Express (PCIe). With the rising frequency and sophistication of digital attacks, ensuring data integrity, confidentiality, and authenticity during PCIe transport… Read More
Tag: SPDM
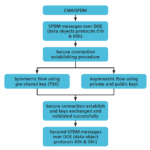
Siemens EDA Offers a Comprehensive Guide to PCIe® Transport Security
It is well-known that there is more data being generated all the time. The need to store and process that data with less power and higher throughput dominates design considerations for virtually all systems. There is another dimension to the problem – ensuring the data is secure as all this movement and processing occurs. Within… Read More
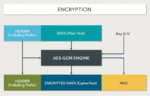
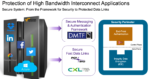
The Heart of Trust in the Cloud. Hardware Security IP
You might think that cloud services run on never-ending racks of servers and switches in giant datacenters. But what they really run on is trust. Trust that your data (or your client’s data) is absolutely tamper-proof inside that datacenter. Significantly more secure than it would be if you tried to manage the same operations in… Read More