Crossing the Chasm by Geoffrey Moore (not that G. Moore!) is one of the most well known books on high technology marketing. When I worked at VaST, Mohr Davidow Ventures (MDV) invested in us and Moore (not Mohr), who was a partner there, spent an afternoon with us brainstorming what it would take for us to cross the chasm. Coincidentally,… Read More
Tag: mdv
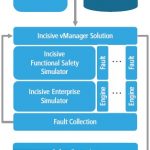
Ensuring Safety Distinctive Design & Verification
In today’s world where every device functions intelligently, it automatically becomes active on any kind of stimulus. The problem with such intelligence is that it can function unfavorably on any kind of bad stimulus. As the devices are complex enough in the form of SoCs (which at advanced process nodes are more susceptible to … Read More
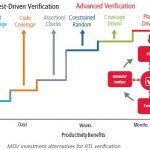
Effective Verification Coverage through UVM & MDV
In the current semiconductor design landscape, the design size and complexity of SoCs has grown to large extent with stable tools and technologies that can take care of integrating several IPs together. With that mammoth growth in designs, verification flows are evolving continuously to tackle the verification challenges … Read More
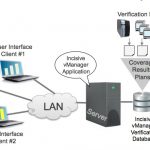
SoC Functional Verification Planning and Management Goes Big
Big SoC designs typically break existing EDA tools and old methodologies, which then give rise to new EDA tools and methodologies out of necessity. Such is the case with the daunting task of verification planning and management where terabytes of data have simply swamped older EDA tools, making them unpleasant and ineffective… Read More