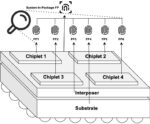
In the quest to secure the authenticity and ownership of advanced integrated circuit (IC) packages, a novel approach has been introduced in this paper that capitalizes on the inherent physical discrepancies within these components. This method, distinct from traditional strategies like physical unclonable functions (PUFs)… Read More